CyberLympha DATAPK
OVERVIEW
CL DATAPK
CL DATAPK offers the necessary equipment and services for upholding asset security. It is conceived and built with the goal of quickly identifying and averting security incidents. It is a complete system for monitoring and analyzing ICS security. CL DATAPK is based on a solid combination of well-known IT security technologies, findings from recent research on ICS/OT security, and extensive practical experience obtained from working on commercial applications.
CONSTANT SECURITY MONITORING
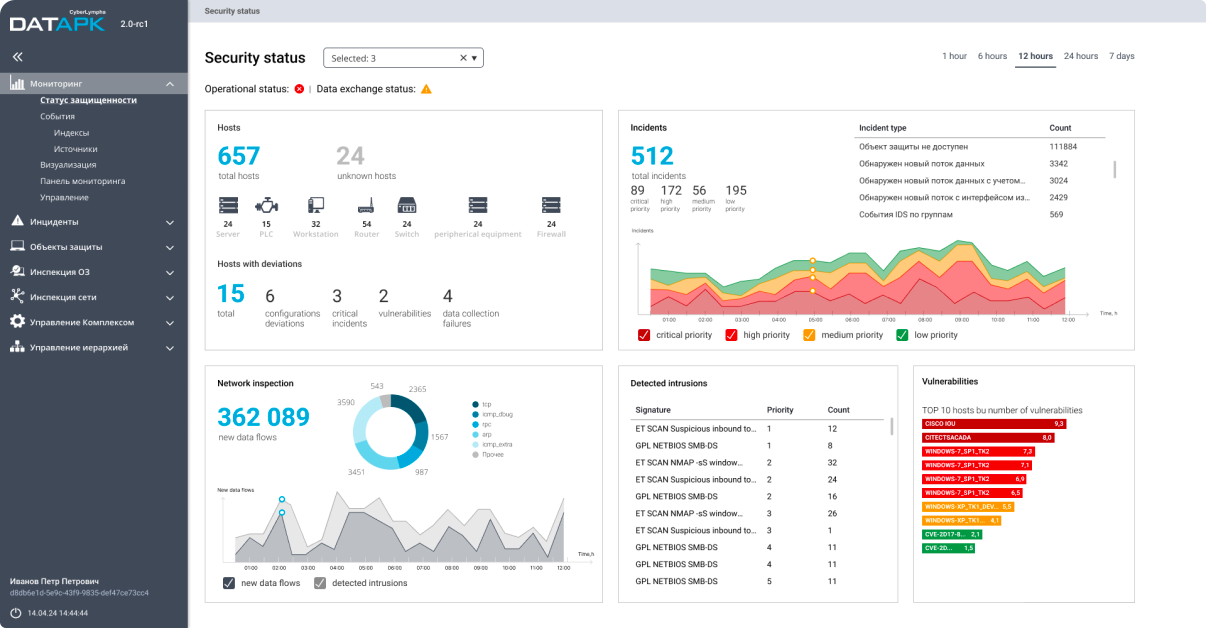
About CL DATAPK
CL DATAPK was designed and developed with a focus on discovering and preventing security incidents at the earliest stage possible. It is a cornerstone of the CyberLympha security platform – a comprehensive ICS security monitoring and analysis solution.
CL DATAPK Crucial Tools
CL DATAPK is based on a robust composition of well-established IT security technologies, results of contemporary studies in the field of ICS/OT security, and deep practical expertise gained on commercial projects. CL DATAPK provides crucial tools and services essential for maintaining asset security:
- Monitor deviations from the reference system model and detect illegitimate changes in protected control systems
- Discover and manage assets, subject to critical vulnerabilities
- Detect exploitation attacks and monitor incident statuses from detection to remediation
- Collect and correlate security events from the assets
- Drive regulatory compliance with state and corporate policies regarding asset cybersecurity
- No agent software required for installation on the ICS components
- Minimum network load
- Various hardware support, incl. industrial appliances
- Several operation modes available for various ICS applications and desired interaction levels
- Local and centralized management
- Seamless integration with corporate security monitoring and/or SIEM systems
- Asset catalogue: automated ICS asset discovery and change management
- Security events management: collection, normalization, and correlation
- Config management: collection and anomaly detection
- Compliance & security status control: vulnerability detection for ICS assets, compliance state analysis for governmental and corporate policies
Is Your Organisation Tech-Ready for the Future?
Get in touch with our specialists and receive a free consultation today.