Cybersecurity
OVERVIEW
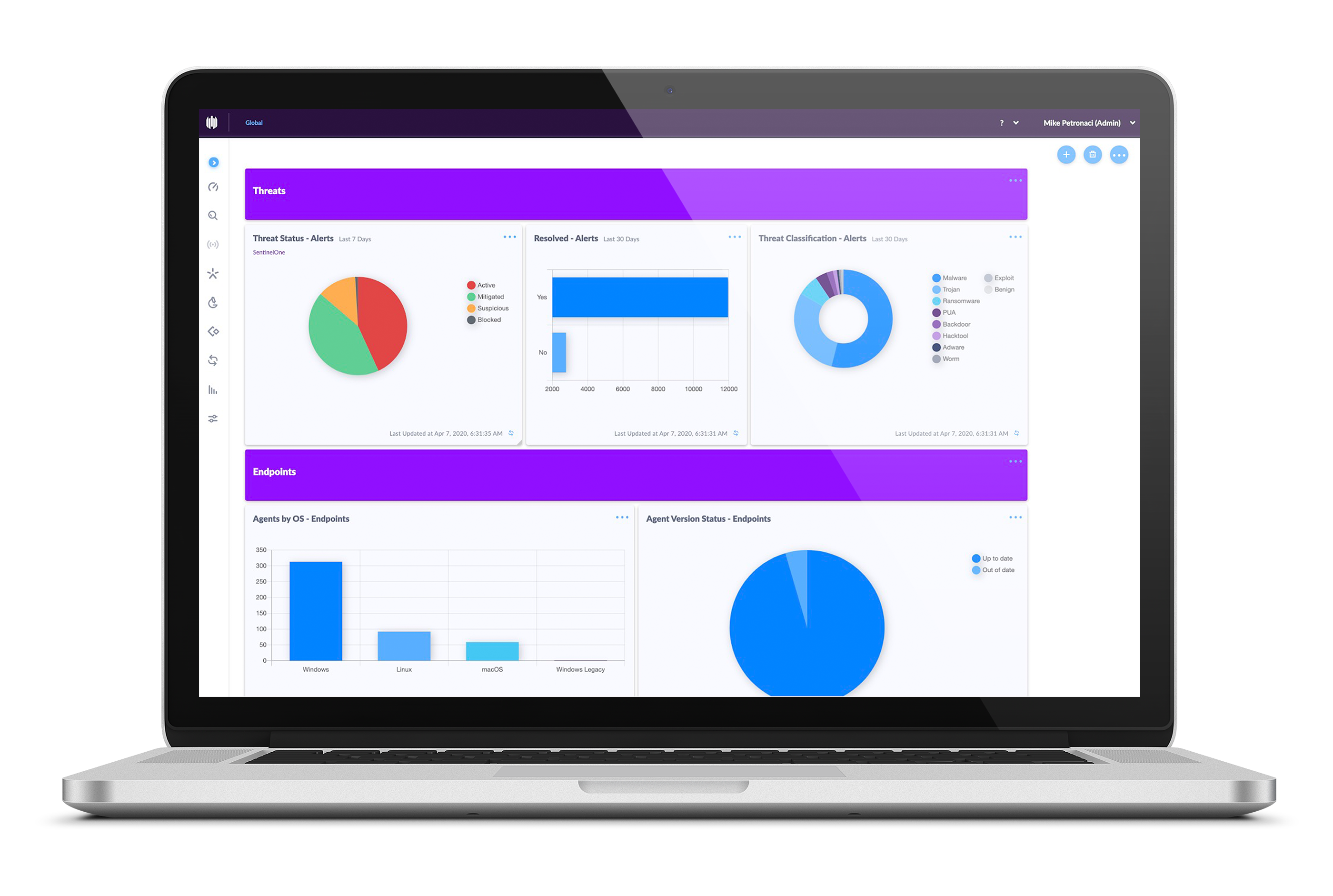
SentinelOne
In the battle against ever-evolving cyber threats, we need to act faster and smarter than what’s possible with human-powered technology. SentinelOne is autonomous cybersecurity built for what’s next. SentinelOne is redefining cybersecurity by pushing the boundaries of autonomous technology. Empowering modern enterprises to defend faster, at a greater scale, and with higher accuracy across their entire attack surface.
SENTINELONE IS REDEFINING CYBERSECURITY
Pushing the Boundaries of Autonomous Technology
The state of cybersecurity is ever-changing. The challenges of today are nothing like those of tomorrow. Threats are evolving and using automation to their advantage. Our goal is to thwart every attack, every second of every day. Our Singularity Platform immediately guards against cyberattacks, doing so with greater speed, scale, and accuracy than any single person or even a large group of people could.

ENDPOINT DETECTION AND RESPONSE
SentinelOne ActiveEDR
ActiveEDR solves the problems of EDR as you know it by tracking and contextualizing everything on a device. ActiveEDR is able to identify malicious acts in real-time, automating the required responses and allowing easy threat hunting by searching on a single IOC. ActiveEDR is delivered via SentinelOne’s single agent, single codebase, single console architecture. Going beyond traditional antivirus and EDR solutions, ActiveEDR, powered by SentinelOne’s proprietary TrueContext technology, allows security teams to quickly understand the story and root cause behind threat actors and autonomously respond, without any reliance on cloud resources.
Solution Benefits:
- Get high efficacy, actionable threat detection without the noise.
- Rapidly uncover and contain advanced threats to reduce incident dwell time and time to resolution.
- Get a complete understanding of the root cause to close existing gaps.
- Empower and uplevel the security team with an easy-to-use, intuitive product.
- Reduce SOC burden by automating manual tasks with automated correlation and one-click remediation.
- Single cloud-delivered platform with true multitenant capabilities to address the needs of global enterprises and MSSPs.
- Best-in-industry coverage across Linux, macOS, and Windows.
- Affordable EDR data retention of 365 days+ for full historical analysis.
Solution Highlights:
- Real-time detection and remediation of complex threats with no need for human intervention.
- Accelerated triage and root cause analysis with incident insights and the best MITRE ATT&CK alignment on the market, with or without MDR.
- Integrated threat intelligence for detection and enrichment from leading 3rd party feeds as well as our proprietary sources.
- Patented 1-Click Remediation & Rollback.
- Intuitive user experience reduces the skills required to add threat hunting to your security operations.
- Data retention options to suit every need, from 14 to 365+ days. Hunt by MITRE ATT&CK Technique.
- Uncompromising protection across Windows, Linux, and macOS endpoints – physical, virtual, container – cloud, or data center.
- Rapid deployment interoperability features ensure a fast, smooth rollout.
- RESTful APIs and pre-built integrations to various Enterprise applications and services.
Is Your Organisation Tech-Ready for the Future?
Get in touch with our specialists and receive a free consultation today.